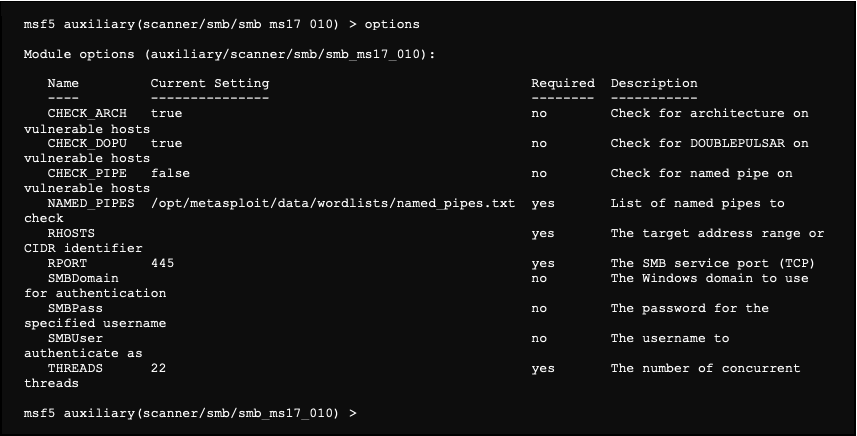
GitHub - TaroballzChen/CVE-2022-40684-metasploit-scanner: An authentication bypass using an alternate path or channel in Fortinet product
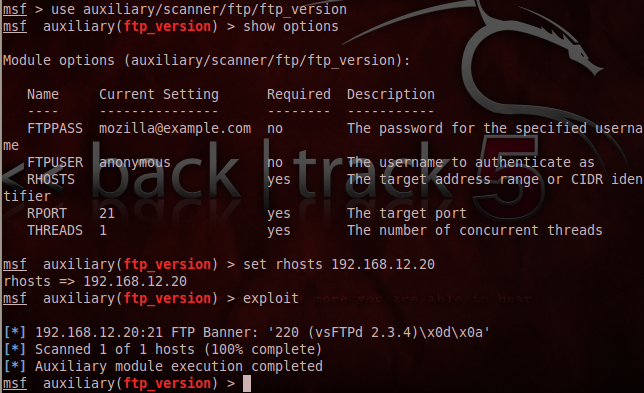
Metasploitable 2.0 Tutorial Part 2: Scanning for Network Services with Metasploit – CYBER ARMS – Computer Security
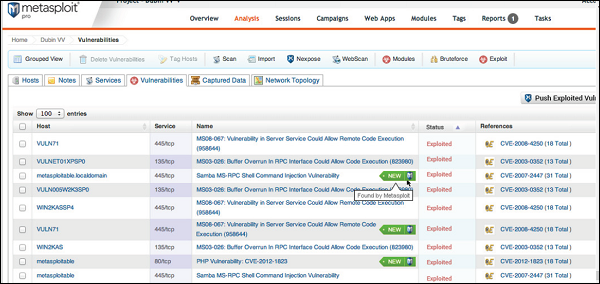
![Metasploit Auxiliaries for Web Application enumeration and scanning - Metasploit Revealed: Secrets of the Expert Pentester [Book] Metasploit Auxiliaries for Web Application enumeration and scanning - Metasploit Revealed: Secrets of the Expert Pentester [Book]](https://www.oreilly.com/api/v2/epubs/9781788624596/files/assets/15d23931-4396-4e2e-8b6e-6c4a90c7f021.jpg)

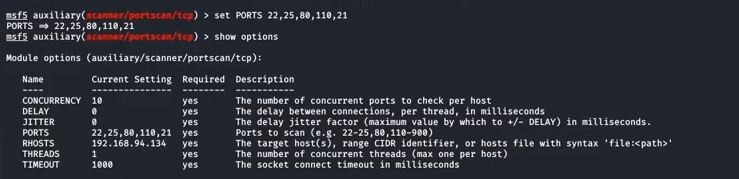

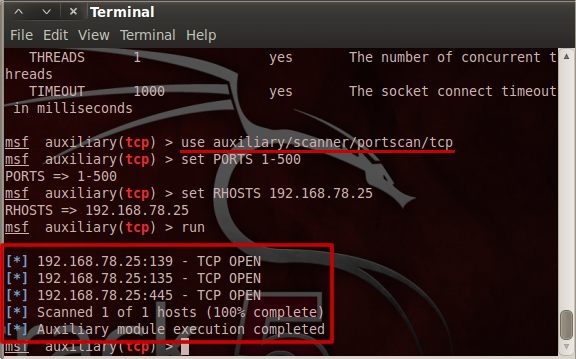


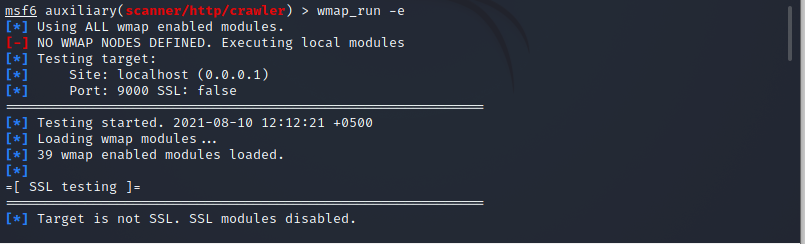
![UDP scanning with Metasploit - Kali Linux Network Scanning Cookbook - Second Edition [Book] UDP scanning with Metasploit - Kali Linux Network Scanning Cookbook - Second Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781787287907/files/assets/image103.jpg)
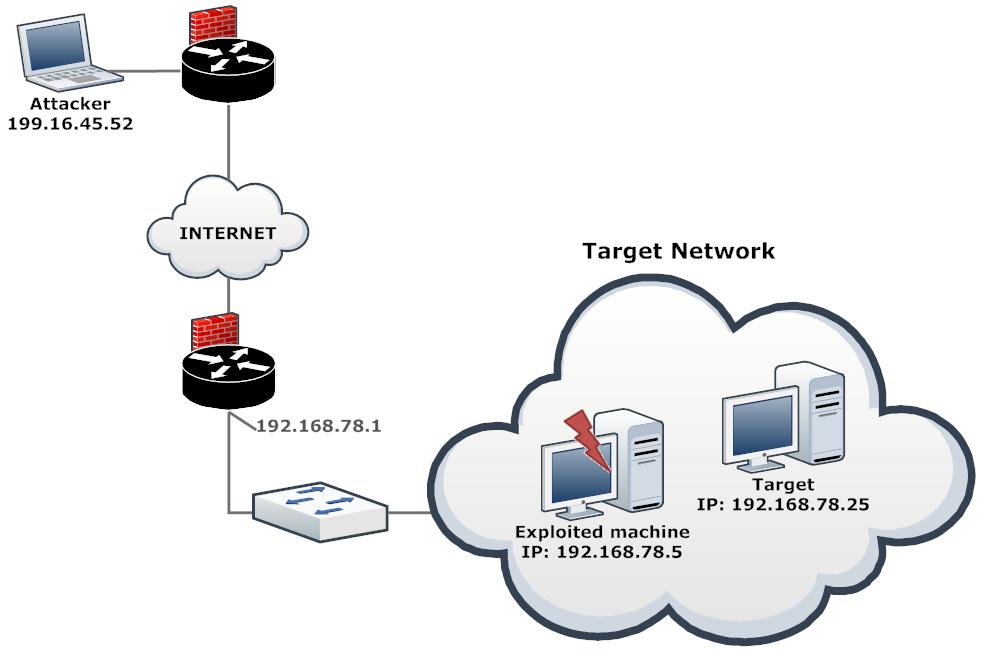
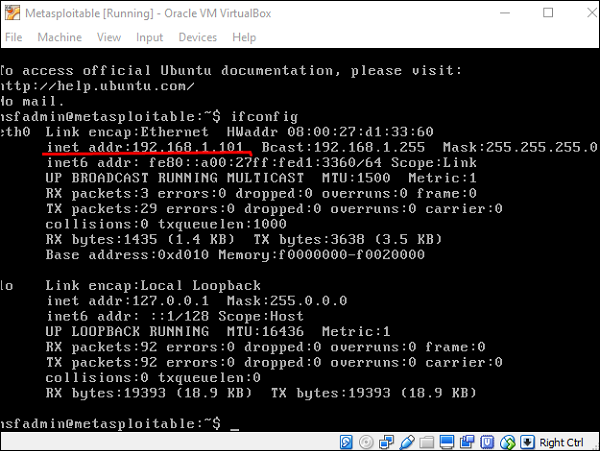
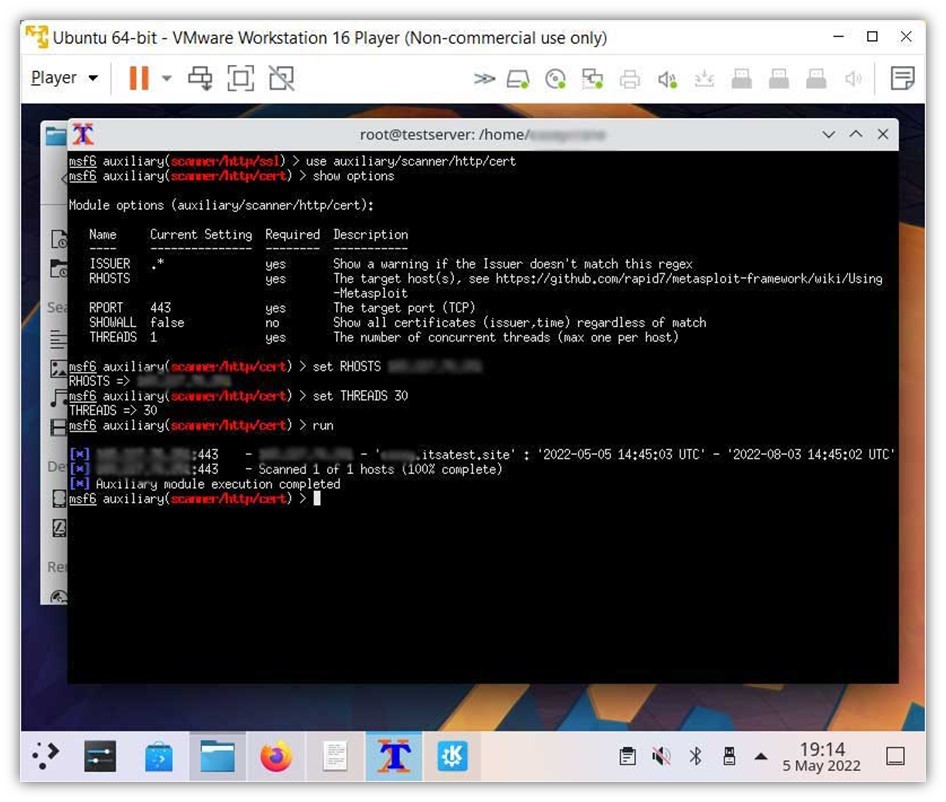
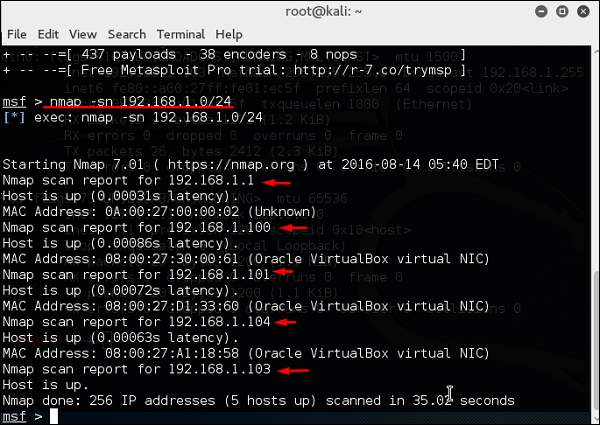
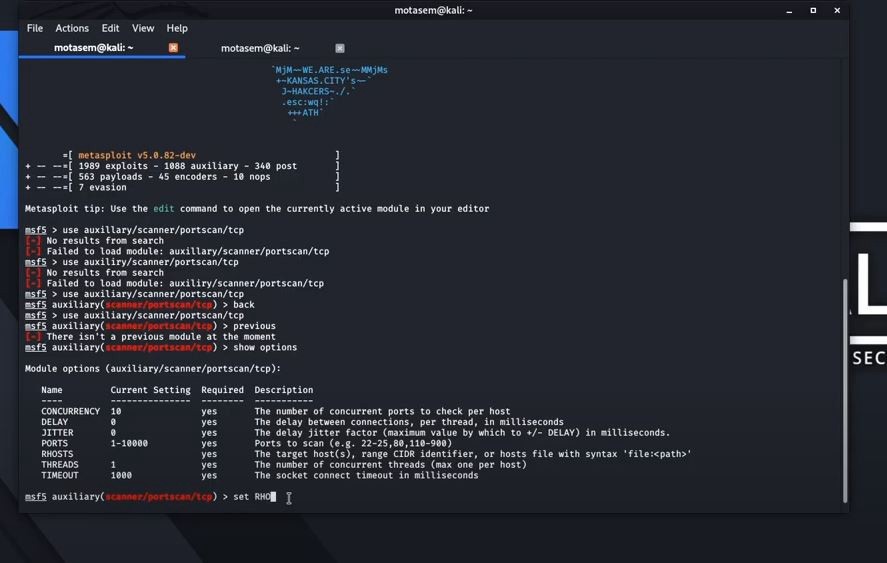

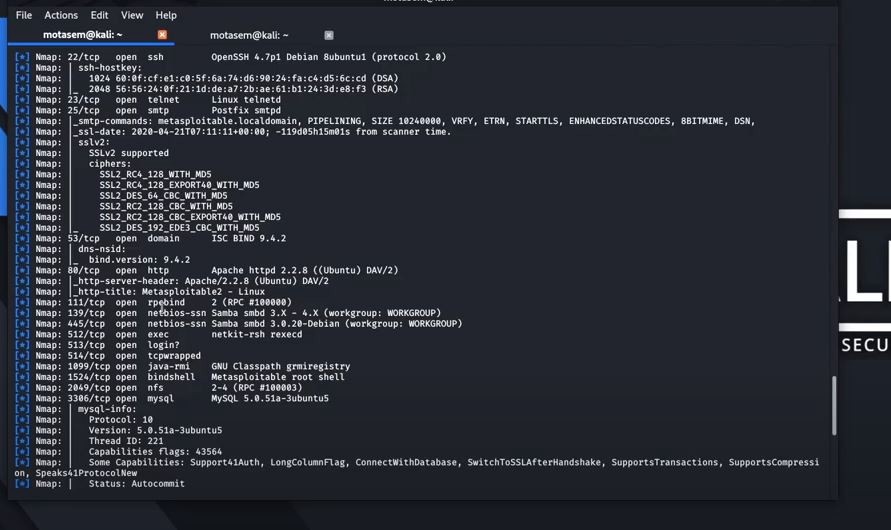


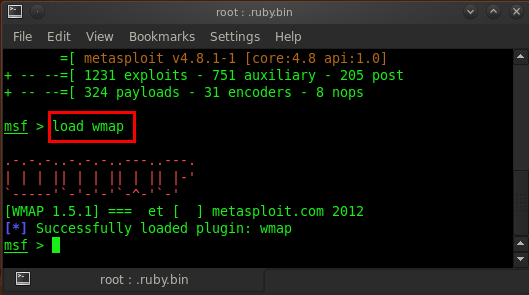

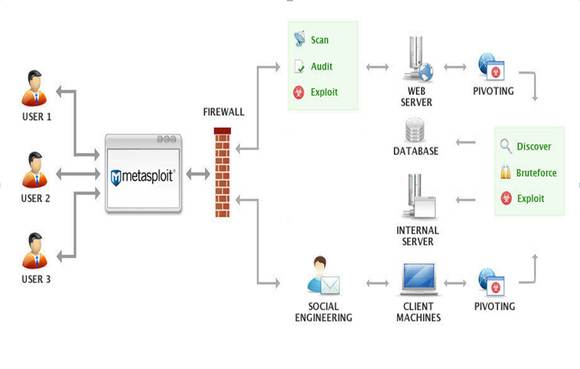
![Stealth scanning with Metasploit - Kali Linux Network Scanning Cookbook - Second Edition [Book] Stealth scanning with Metasploit - Kali Linux Network Scanning Cookbook - Second Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781787287907/files/assets/image113.jpg)